Currently, Quick Config Setup allows you to deploy the SmartWorkspaces solution in an existing environment or install it from zero if necessary.
Types of deployments:
- Full deployment: both the resource domain (domain where the infrastructure VMs reside) and the domain where the VDIs / SDIs and users will reside are generated.
- Mixed deployment: the Resource domain that integrates with an existing domain is autogenerated. A trust relationship between domains is created.
- Full integration: Resource domain is not generated, since the entire solution is installed in an existing domain. For this deployment, no trust relationship is created.
Remember that points 2 and 3 will only be available for non-NFR licenses.
Requirements
- Not available in NFR (demo models).
- If a domain controller is available, AD functional level should be Windows 2008 R2 or higher.
- The domains should mutually resolve one another. This is automatically configured during automatic deployment.
- DHCP configured if use Full integration deployment.
- WinRM configurated in Domain Controllers.
-
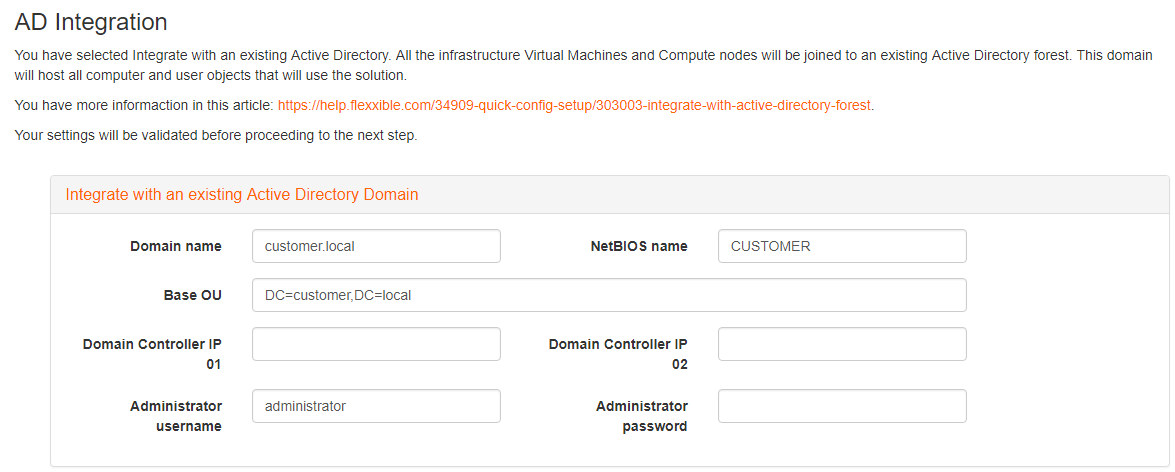
During deployment, in the section AD Integration, you need to enter the domain admin credentials because deployment will perform the following tasks:
- Active Directory:
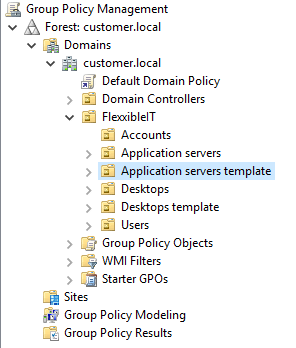
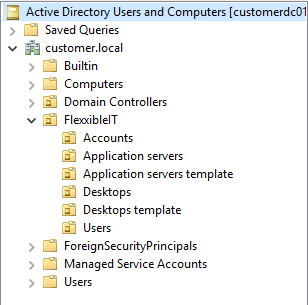
- Create OU, block inheritance and delegate OU permissions
- Create computer accounts
- Create users accounts
- Create groups
- Create MSA accounts
- Join computer to domain and generate blobs
- Delegate OU permissions to cluster computer account
- DNS (Active Directory-Integrated DNS):
- Create DNS records
- Group policy (GPO):
- Import GPOs
- Modify values in group policies (only imported GPOs)
- Link GPOs to root OU and child OUs
- Export and backup GPOs (only imported GPOs)
- Domain Controller server:
- Create temporary folder and files in Domain Controller (C:\Temp)
- For Mixed deployment, following tasks will also be carried out:
- Create forwarder conditional (AD partition)
- A trusted relationship
- Coming soon!
- Active Directory:
Integration process
The following features are checked for installation:
- Group Policy Management (if required, install with Install-WindowsFeature GPMC)
- Active Directory module for Windows PowerShell (if required, they should be installed with Install-WindowsFeature RSAT-AD-PowerShell)
- DFS Management tools: RSAT-DFS-Mgmt-Con powershell module
The process checks the health status of the domain controller:
- Check AD functional level: Check that the version of the AD functional level (domain and forest) is Windows 2008 R2 or higher
- Check that the netlogon is correct: dcdiag /test: netlogons
- Check that the replication does not present any problems: dcdiag /test: Replications
- MSA accounts creation
- Group Policy creation
How to perform each deployment
Full deployment
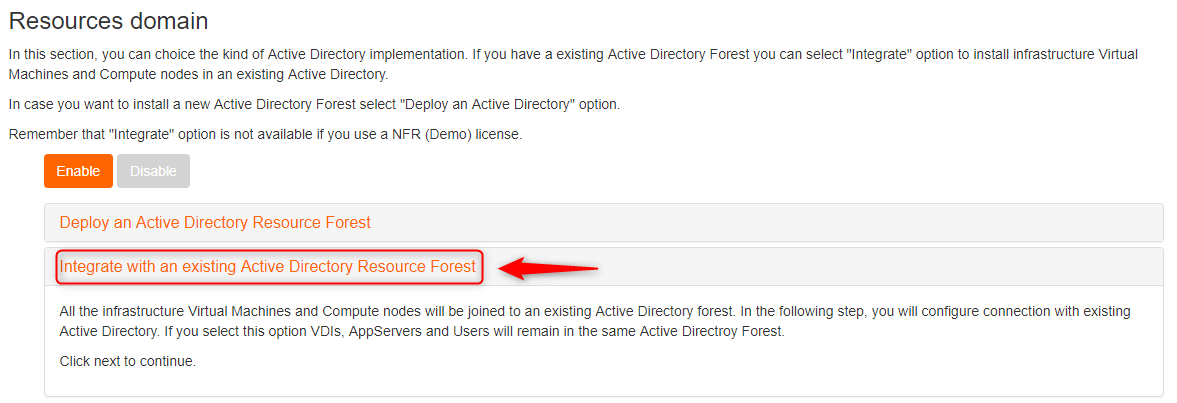
Select first option 'Deploy an Active Directory Resource forest'
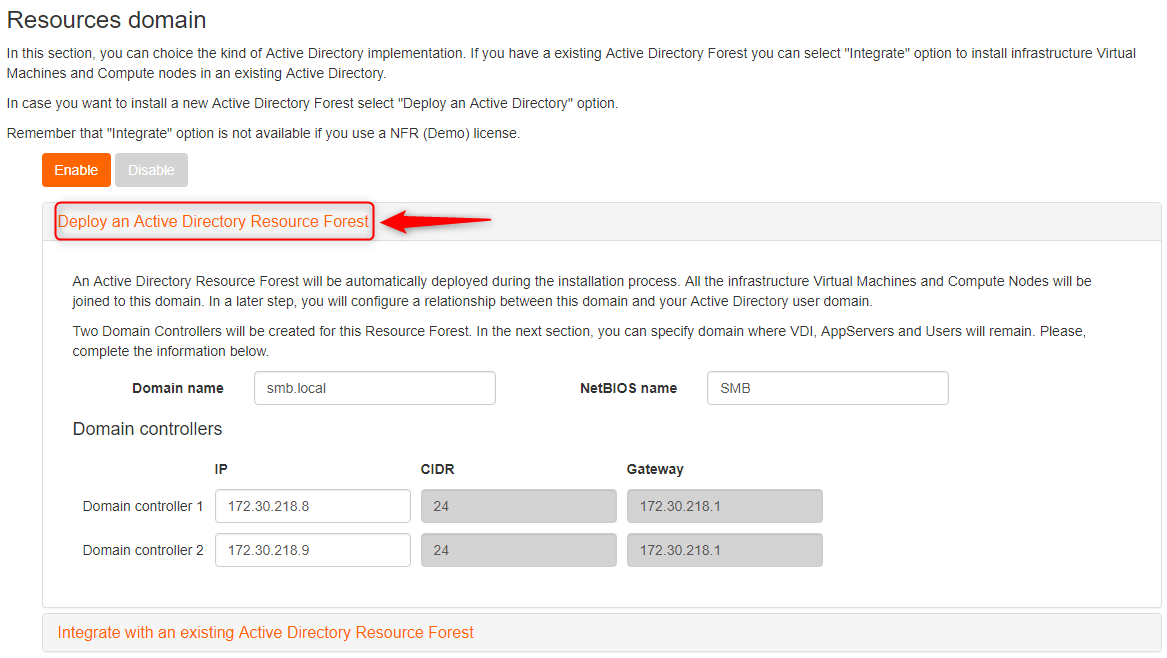
Select first option 'Create new Active Directory Domain'
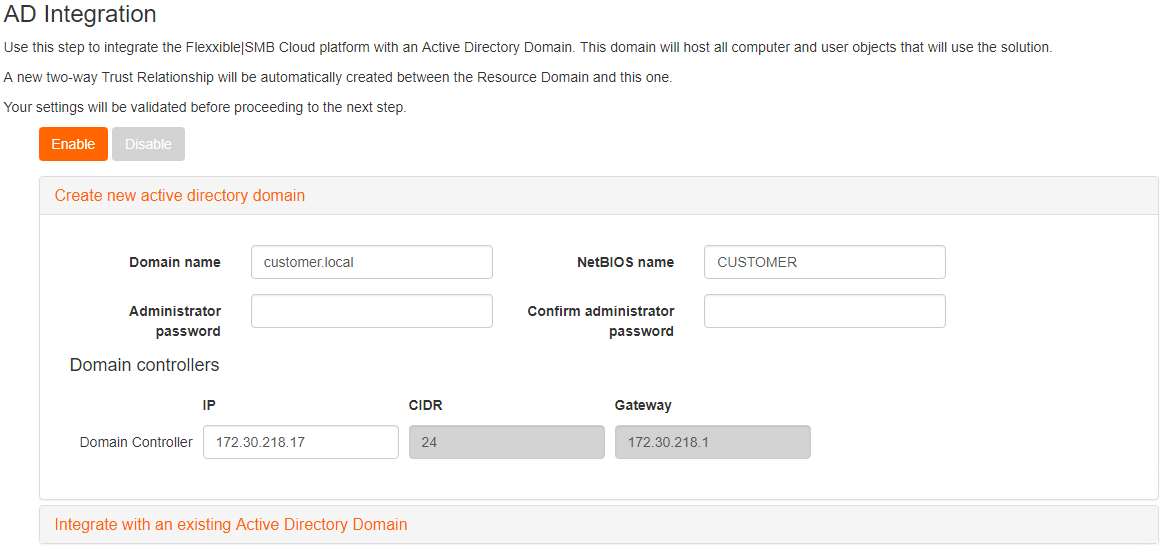
Mixed deployment
Select first option 'Deploy an Active Directory Resource forest'
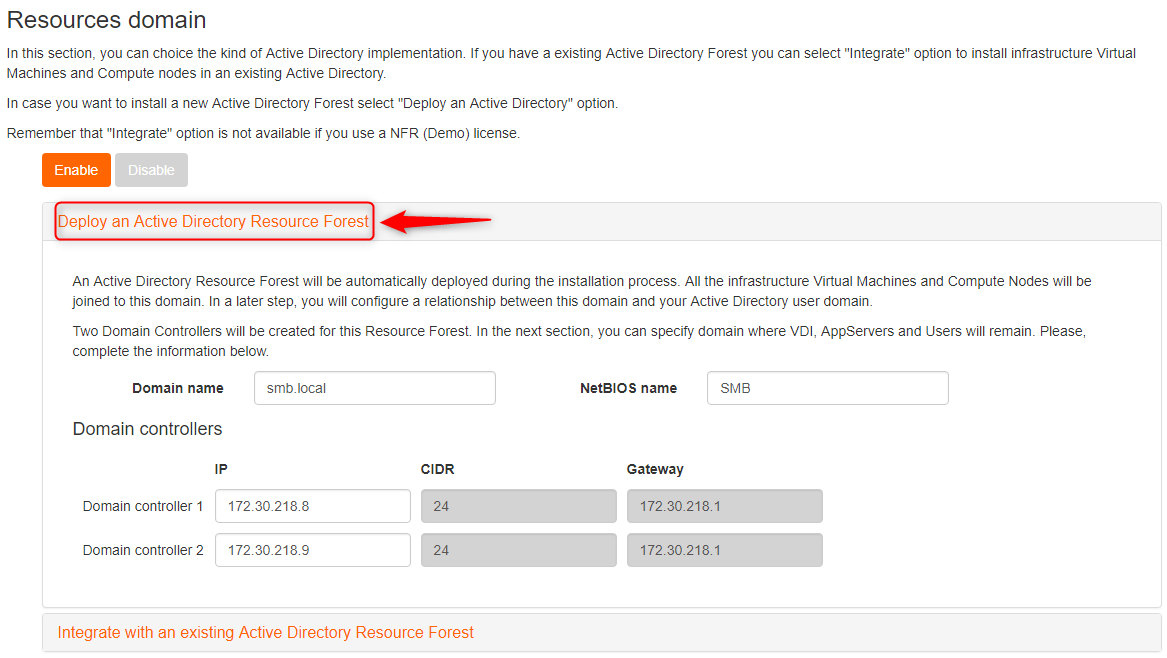
Select 'Integrate with an existing Active Directory Domain'
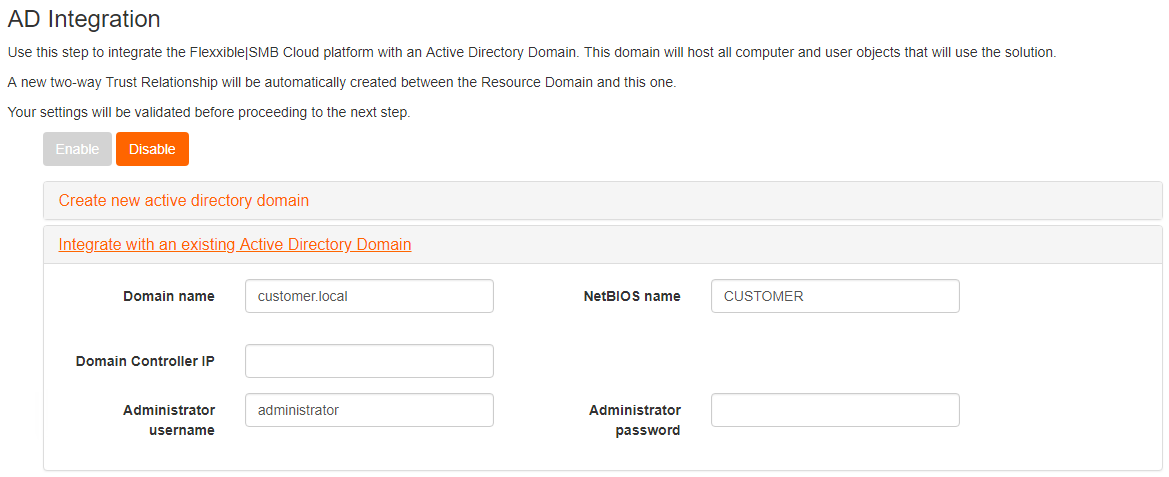
Full integration
Select second option 'Integrate with an existing Active Directory Resource forest'
Mixed deployment
When you choose to integrate your Windows domain into the deployment, a series of changes are made to your domain controller to integrate it into the automatic orchestration process.
During the domain integration process, a trust relationship will be created between the resources domain, so you'll have an environment that works in two domains:
- Desktops, application servers and templates will be in the customer domain.
- Citrix servers, hypervisor and the rest of the infrastructure will be in the resource domain.
In addition, a number of requirements must be met, such as:
- Conditional forwarders are created in both domains so that can be resolved between them
- GPOs are imported and linked according to the configuration entered in the QCS, these policies can be found at http://flxpol.azurewebsites.net
-
Security groups, to manage the activation of functionalities on users and resources, new groups will be created of within the base organizational unit. The list of groups to be created is as follows:
- Template Designers: users with permission to edit templates
- Users: all users in the virtualization environment
- Managers: administrators of the environment
- Remote support team: users who can provide remote assistance to other users
- Users with USB redirection: enable USB redirection
- Users with COM redirection: activation of COM redirection
- Users with LPT1 redirection: activation of LPT1 redirection
- Users with Local Units redirection: enable redirection of local units
- Users with Audio redirection: enable audio redirection
- Users with Printer redirection: enable printer redirection
- Users with TWAIN redirection: enable TWAIN redirection
- Users with Network drive redirection: enable network drive redirection