Workers host the Flexxible|SUITE services and orchestration and process the different operations that run in the background or are requested by the web console operators. They also collect health, diagnostic, and status information from the different VCC roles, VDI desktops, and application servers.
Worker types
Primary workers should run all the Flexxible|SUITE services. There must be as many primary workers as nodes in the reference Windows Failover Cluster.
Secondary workers are accessories, to alleviate the workload of primary workers when there is a big amount of concurrent sessions and can only run some of the Flexxible|SUITE services.
Note: which Flexxible|SUITE services can be installed in which worker types are described later in this document.
Hardware requirements
Depending on the number of concurrent sessions different dimensioning for hardware is recommended as shown in the following table:
| Primary workers | Additional secondary workers (2 vCPUs, 4 GB RAM) |
||
| Max. concurrent sessions + reporters | vCPUs | RAM GB | |
| 2000 | 4 | 4 | - |
| 5000 | 4 | 8 | 2 |
| 10000 | 8 | 16 | 4 |
| 15000 | 12 | 24 | 6 |
| 20000 | 16 | 32 | 8 |
| >20000 | Custom design | ||
Please note:
- The number of sessions includes any kind of session: VDI, SDI, and application, including connected and disconnected sessions. A reporter is any machine running the VDIClient Service (VDI desktops, infrastructure VCC Role VMs, VDI Appliances, servers, Endpoints, etc). The sum of sessions and reporters determines the amount of work that the workers will have to handle.
- Secondary workers have a fixed hardware specification, while the primary workers hardware dimensioning will depend on the number of concurrent sessions that they must handle
These values represent just guidelines to dimension an installation of Flexxible|SUITE. The real amount of work to handle is particular to every installation and dynamic over time. It will be affected by many factors like:
- the kind of sessions. For example, VDI sessions produce more workload than application sessions
- the number of VDI desktops, and application servers. Every one of these VMs runs a VDIClient service instance that augments the workload to handle.
- the frequency with which VDIClient service reports health and status information and the retention of history tables. Big history tables require more power to be updated.
- the behavior of VDI session users. If the user usually disconnects when they go home instead of closing the session, the open session continues to report information
Software requirements
Operating system
Microsoft Windows Server 2016 Datacenter Core is advised, although Windows Server 2012 R2 or later is supported.
Note: if you are going to work with Citrix DaaS in your Flexxible|SUITE installation, you can't use a Windows Server Core edition, since the Citrix Remote PowerShell SDK requires it.
SQL Server
Please, refer to the SQL Server requirements article.
Windows features/roles
Enable the needed Windows features by executing the following Powershell fragment:
$Features = "NET-Framework-Core","NET-Framework-45-Core","RSAT-RemoteAccess-Powershell","Hyper-V-PowerShell","RSAT-AD-PowerShell", "GPMC"
foreach ($Feature in $Features) {
Write-Host "Instalando $Feature" -f Yellow
if (!(Get-WindowsFeature $Feature).Installed) {
Install-WindowsFeature $Feature -IncludeManagementTools -Source D:\sources\sxs
}
}* The "Active Directory module for Windows PowerShell" (RSAT-AD-PowerShell) is required from Flexxible|SUITE v 4.10
Windows firewall
Several Windows firewall rules must be enabled or created. To do it execute the following PowerShell fragment:
New-NetFirewallRule -DisplayName "VDICLIENT-TCP-INBOUND" -Direction Inbound -Protocol TCP -LocalPort 1236,1237 -Action Allow
Get-NetFirewallRule | ? {$_.DisplayName -like "*File*"} | Set-NetFirewallRule -Enabled true
Get-NetFirewallRule | ? {$_.DisplayName -like "*Windows Management Instru*"} | Set-NetFirewallRule -Enabled true
Get-NetFirewallRule | ? {$_.DisplayName -like "*Remote Desktop*"} | Set-NetFirewallRule -Enabled true
Get-NetFirewallRule | ? {$_.DisplayName -like "*Remote Event Log Management*"} | Set-NetFirewallRule -Enabled true
Get-NetFirewallRule | ? {$_.DisplayName -like "*Remote Service Management*"} | Set-NetFirewallRule -Enabled true
Get-NetFirewallRule | ? {$_.DisplayName -like "*Remote Volume Management*"} | Set-NetFirewallRule -Enabled true
Get-NetFirewallRule | ? {$_.DisplayName -like "*Windows Firewall Remote Management*"} | Set-NetFirewallRule -Enabled true
Get-NetFirewallRule | ? {$_.DisplayName -like "*Remote Scheduled Tasks Management*"} | Set-NetFirewallRule -Enabled trueInternet connection
Flexxible|SUITE can use many services that require access to the Internet (Azure, Citrix DaaS, etc.)
In this scenario, please check that Flexxible Workers have a direct connection to the Internet or configure the proxy settings if needed.
Enable TLS 1.2
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
gMSA Account
An Active Directory Group Managed Service Account should be created for the machine, so there is no need to worry about password management and expiration.
Note: if you can't use gMSAs, a conventional account can also be used as the identity for the Flexxible|SUITE services, and the password should be updated according to the expiration policy.
The sample scripts in this document assume that you are using a gMSA account.
Once the account is created, it must be installed.
To know the name of the gMSA assigned to the server execute the following PowerShell:
$MSAToThisVM = (Get-ADServiceAccount -Filter * -Properties * | ? {$_.PrincipalsAllowedToRetrieveManagedPassword -like "*$env:COMPUTERNAME*"}).NameOr, if you already know the account name:
$MSAToThisVM = "MSA_Name"
Then install the gMSA account:
Install-ADServiceAccount $MSAToThisVM
Temp folder
To host diagnostic log files produced by Flexxible|SUITE, create a c:\temp folder:
if (!(Test-Path C:\temp)) {New-Item C:\temp -ItemType Directory}The files generated in this folder are automatically deleted after a time.
Group policies
The following group policies must be created and applied to the OU containing the computer account:
Configuration - VDIClient settings
This group policy enables connectivity with the rest of the Flexxible|SUITE VCC roles, and should define the following settings and values:
ADQueue config
Contains an inventory of VCC Worker roles, in the form of a semicolon-separated list of FQDNs (or IPv4 addresses) and ports where the Flexxible|SUITE Queue listener service is installed and listening:
Worker01.domain.local:1236; Worker01.domain.local:1237; Worker02.domain.local:1236; Worker02.domain.local:1237
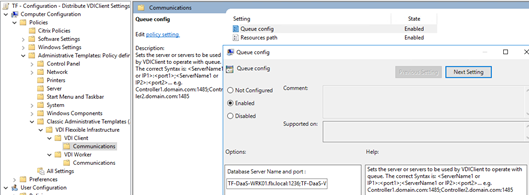 Resources path
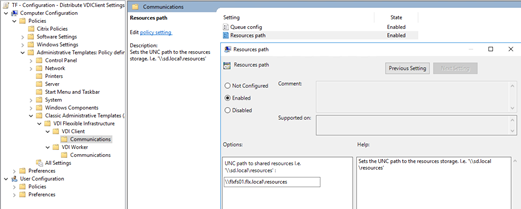
Resources path
The root UNC path for the Flexxible|SUITE resources repository:
\\FS01.domain.local\resources
AD Group
For the proper functioning of the services, you must ensure that the Flexxible VDI Services account is a member of the Administrators group for each worker.
Configuration - VDIWorker settings
This group policy enables connectivity with the rest of the Flexxible|SUITE VCC roles and with the database, and should define the following settings and values:
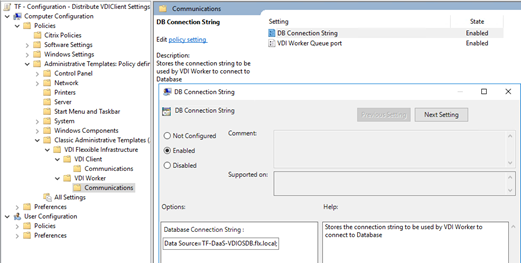
DB connection string
The connection string to the VDIManager database, which is the Flexxible|SUITE database:
Data Source=AlwaysOnListener.domain.local;Initial Catalog=VDIManager;Persist Security Info=True;Integrated Security=SSPI;MultiSubnetFailover=Yes;
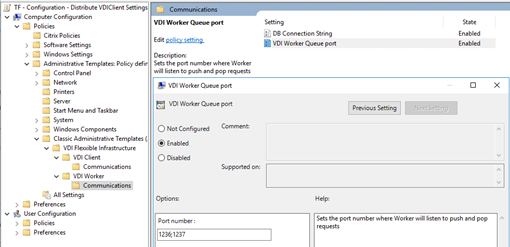
VDI Worker Queue Port
The semicolon-separated list of TCP ports that the Flexxible|SUITE Queue Listener service is listening to. Coordination messages of the different SUITE components are transmitted using these ports:
1236;1237
Once these group policies are defined, they should look similar to this example:
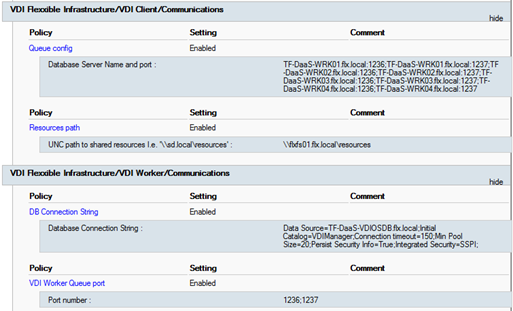
Credentials delegation in a multi-hop environment using an SMB shared folder over SCVMM
When creating Templates and Servers, in environments through shared storage using an SMB shared folder, it could be necessary to delegate credentials to authenticate against the shared resource.
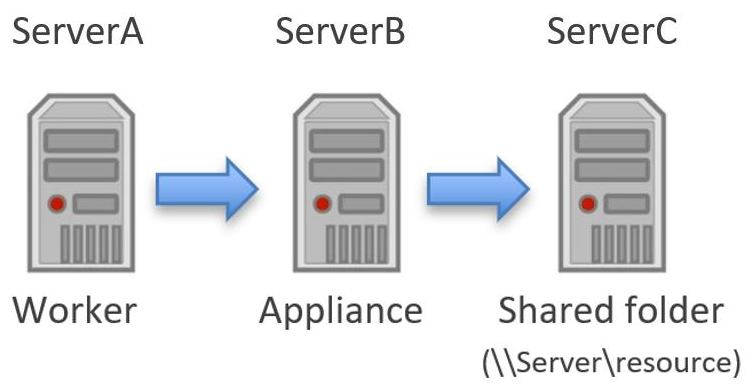
In this case, it may be necessary a specific setup, depending on the authentication method during the VMs creation.
You could find more info in the following articles:
- Hyper-V over SMB: Set SMB constrained delegation via PowerShell.
- Making the second hop in PowerShell Remoting
VDIClient service
The VDIClient service allows the supervision and management of the worker machine by Flexxible|SUITE.
To install it, execute the Setup.exe file from the resources path subfolder Clients\Installers\VDIClientService and use the default options.
To uninstall the service, use the "Add or remove programs" Windows dialog. If the service could'nt be removed this way, an alternate way is:
- Stop the service from the services console
- Execute the following command from an elevated command-prompt:
sc delete "Flexxible secure|desktop VDIClient"
Citrix Virtual Apps & Desktops snapins
These snapins allow the Flexxible|SUITE web console to work with Citrix Virtual Apps & Desktops.
If your Flexxible|SUITE installation is exclusively connecting to on-premise Citrix Virtual Apps & Desktops installations, you can use the snapins found in the Citrix Virtual Apps & Desktops DVD or .ISO, in the x64\Citrix Desktop Delivery Controller folder:
Please use the snapins from the newest version among the Citrix Virtual Apps & Desktops farms that you are planning to use.
Every .msi file containing the "Snapin" word in the name must be installed by double-clicking it.
Once the snapins are installed, they should appear in the Windows "Programs and Features" dialog:
On the other hand, if your Flexxible|SUITE installation will work with at least one Citrix DaaS broker farm, then you must install the Citrix Remote PowerShell SDK (you can download it from https://download.apps.cloud.com/CitrixPoshSdk.exe) to allow Flexxible|SUITE to work with Citrix DaaS and with on-premise installations of Citrix Virtual Apps & Desktops.
Please, be aware that the Citrix Remote Powershell SDK does not support Windows Server Core editions.
Note: remember that the Citrix DaaS connectors AD computer accounts must be added to the Desktop Delivery Controllers AD group (which name is specified by the setting "DDControllersGroup") and restarted to apply for new membership permissions.
Hypervisor-specific management tools
The following components should be installed depending on which kind of hypervisor is being used in the platform.
Microsoft Hyper-V (System Center Virtual Machine Manager)
For Microsoft Hyper-V, the System Center Virtual Machine Manager console (which includes the necessary PowerShell modules) must be installed from the installation media (SCVMM DVD or .ISO file).
Select only the VMM Console option, not the VMM management server, as indicated by the following sample images:
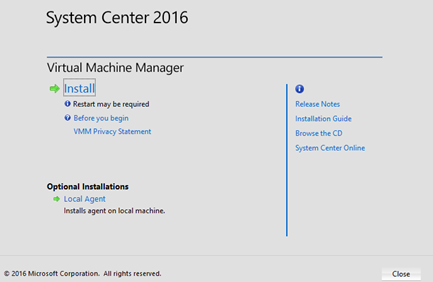
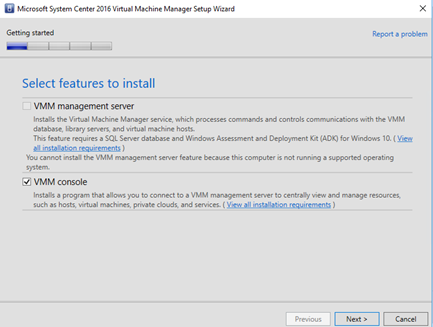
Once the SCVMM console is installed, the last SCVMM RollUp update should be installed, matching the SCVMM RollUp version installed in the SCVMM management server.
You must create a setting in the web console. This setting must be called VMMModulePath (for SCVMM2012), VMMModulePath_2016 (for SCVMM2016) or VMMModulePath_2019 (for SCVMM2019) depending on the version of SCVMM you install in the worker role. This setting is used for SUITE to know where the SCVMM access snapins are installed.
On the other hand, for the proper functioning of Flexxible|SUITE with Hyper-V hypervisor, the "Failover Cluster Module for Windows Powershell" must be enabled.
Enable-WindowsOptionalFeature -Name 'RSAT-Clustering-PowerShell'
Citrix XenServer
XenServer SDK
The SDK is packaged as a ZIP file and is available as a free download from http://www.citrix.com/downloads/citrix-hypervisor/
For Flexxible|SUITE to be able to interact with XenServer, the whole XenServerPSModule folder from the SDK file must be copied to the Windows default PowerShell modules location %WINDIR%\system32\WindowsPowerShell\v1.0\Modules
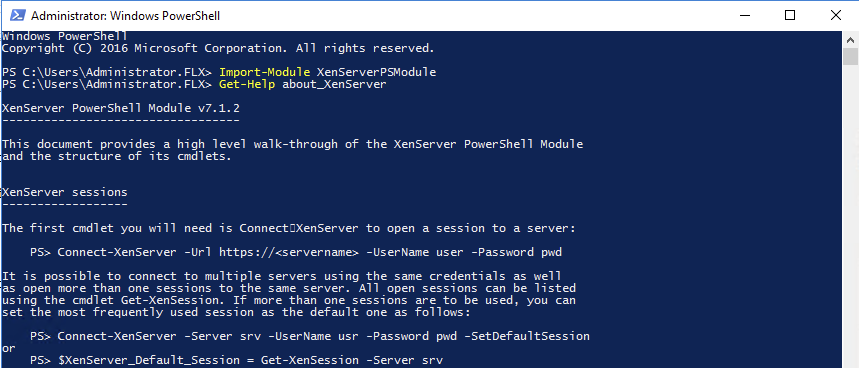
To verify that the module is installed, execute the following PowerShell:
Get-Help about_XenServer
Expected result:
StarWind V2V Image Converter 8.0
The StarWind V2V Image Converter is used to convert disk formats when creating new templates or servers on XenCenter. It can be download from https://www.starwindsoftware.com/converter.
Install the product with the default options.
VMware vSphere
PowerCLI
For VMware vSphere, the PowerCLI Powershell modules must be installed so Flexxible|SUITE can interact with vSphere. If the Worker has internet access, these modules can be installed by executing the following PowerShell fragment:
Install-Module -Name VMware.PowerCLI -AllowClobber -Force
For other configurations, please refer to https://blogs.vmware.com/PowerCLI/2018/01/powercli-offline-installation-walkthrough.html for installation guidelines.
OVF Tool 4.3.0
The Open Virtualization Format Tool is used to create templates or servers on VMware vSphere and can be downloaded from https://code.vmware.com/web/tool/4.3.0/ovf
Install the tool using the default options.
Microsoft Azure
If you plan to use Microsoft Azure as a hypervisor in your Flexxible|SUITE installation, a PowerShell module must be installed in the Worker VCC roles to allow Flexxible|SUITE to interact with Microsoft Azure.
Azure PowerShell Az module
You can download and install the latest supported version of this PowerShell module by following the instructions at http://docs.microsoft.com/en-us/powershell/azure/install-az-ps
Also, you must enable access to the following URLs through the firewall (ports 80- 443):
- login.micrososftonline.com
- management.azure.com
Flexxible|SUITE services
Service instances layout
These are the different Flexxible|SUITE services and the type of workers where they must be installed:
| Name | Installation media folder | Active / passive | Target worker type |
Flexxible secure|desktop WorkerStructure |
VDIWorkerStructure | Yes | Primary only |
Flexxible secure|desktop WorkerActiveDirectory |
VDIWorkerActiveDirectory | Yes | Primary only |
Flexxible secure|desktop Auxiliar |
VDIWorkerAux | No | Primary only |
| Flexxible secure|desktop WorkerAlerts | VDIWorkerAlerts | No | Primary only |
Flexxible secure|desktop Queue |
VDIQueueListener | No | Primary & secondary |
Flexxible secure|desktop WorkerClient |
VDIWorkerClient | No | Primary & secondary |
Flexxible secure|desktop WorkerDesktopOperations |
VDIWorkerDesktopOperations | No | Primary & secondary |
Important: please see https://help.flexxible.com/flexxible-suite-user-guide/active-passive-services-setup for additional required details about the Flexxible|SUITE services configuration.
Installation of a Flexxible|SUITE service
To install the service, execute the Setup.exe file in the service installation media folder with the default options as shown in the following sample images:
Once the service is installed, the service identity must be configured from the services console to use a domain account, as illustrated by the following sample images:
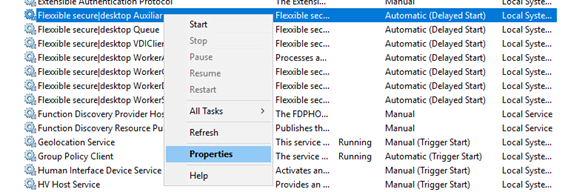
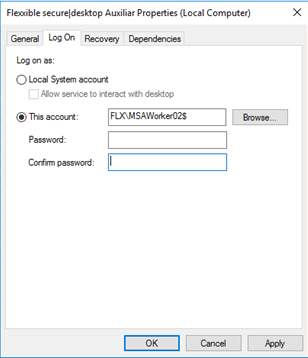
The identity of the services should be a local administrator in the Worker VCC role machine. Usually, an AD group is created in the infrastructure domain and the account(s) used for the Flexxible|SUITE are added to this group, and the group is configured as a local administrator. Then the group name is informed in the Flexxible|SUITE setting "VDIManagerAdminUser".