This article describes the use of computer accounts previously created for desktop or application servers in domains where Flexxible|SUITE is installed.
Both Tenants and Partners can modify the value of these permissions, but they can not create new permissions or delete them.
Integration in restrictive domains
A domain-level field has been added that allows you to specify the start time for synchronization with the Active Directory. This option is only visible if you set the domain to sync automatically.
The option to specify whether you have permission to perform specific actions in the Active Directory has been added at the domain level. The options are:
- Check AD account existence
- Create & edit group policies
- Create and delete computer accounts
- Create internal groups
- Create or update user information
- Create OUs in Base OU
- Delete users
- Force AD Replication
Below there is a description of how to enable automatic synchronization and how to configure domain-level permissions.
Automatic synchronization
Active directory objects of domains registered in Flexxible|SUITE that are in use (for example, groups configured, users assigned to a template, etc.) are cached in the Flexxible|SUITE database and re-synchronized every 4 hours. Objects that are no longer in use are removed from the cache.
Domain and Computer Account Permissions
See “Domain permissions”.
Computer Account Status in a Delivery Group
In the Virtual Desktop Templates and the Application Server Farms views, you can find the list of delivery groups in the tab section. These can be used to serve users on desktops or applications.
If Flexxible|SUITE does not have permission to create and delete computer accounts over the template domain, this list will display additional columns to view the status of the computer accounts assigned to the delivery group for creating new VMs:
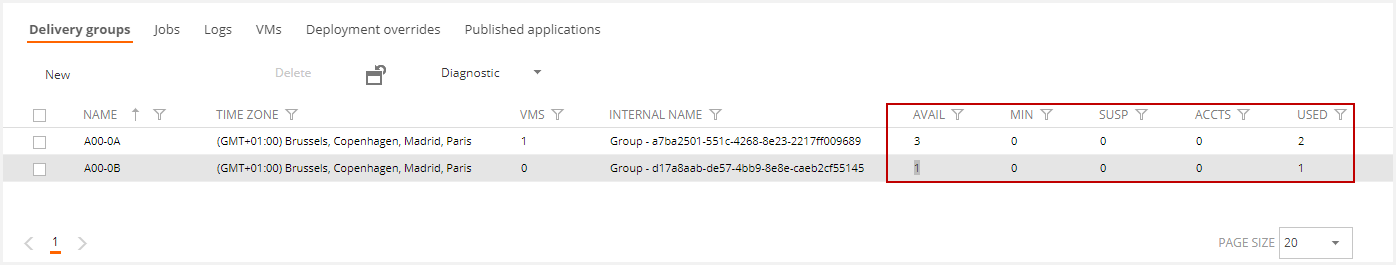
- The "Avail" column indicates how many computer accounts are available for assigning to the new VMs. If this number is less than the set minimum (column "Min"), the value will be highlighted in red.
- The "Used" column indicates how many computer accounts are in use in the VMs in the delivery group.
- The "Susp" column indicates the number of accounts in "Suspect" status, meaning that they are incorrectly formatted, do not exist in Active Directory, or could not be verified. Also flagged as suspicious are the accounts available in the correct format and existing in the domain, but which produce an error when added to a delivery group to create a new VM.
The suspicious accounts will not be used to create new VMs. If there are any accounts in this state, the box is highlighted in red to make the users aware. - The Accts box indicates the total number of team accounts associated with the delivery group, including those available, used, and suspicious.
Adding Computer Accounts to a Delivery Group
When the template associated with a Virtual Desktop Template or Application Server Farm belongs to a domain for which Flexxible|SUITE does not have permissions on computer accounts, a new "Computer accounts" tab is enabled in the detail view of a delivery group. In this tab you could manage these accounts:
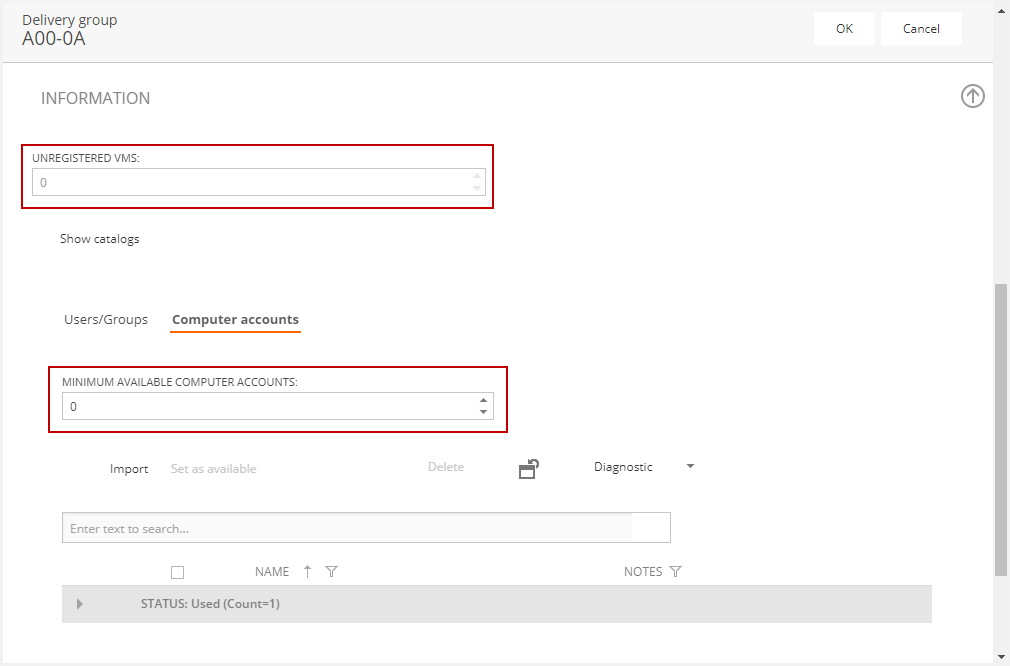
Flexxible|SUITE will activate an alert when the "Minimum available computer accounts" is reached. If you set up this number, these additional accounts can be provisioned.
The list shows the computer accounts associated with the delivery group, grouped by state:
- Available: The computer accounts available to create new VMs. Their format and existence in Active Directory have been validated by adding them to the delivery group, but they are validated again when used during the creation of VMs. If they do not pass the validation, are marked as "Suspect".
- Used: The accounts that are being used by VMs in this delivery group. When you delete the VMs, your computer accounts reappear as available.
-
Suspect: The computer accounts that will be displayed as suspects in the "Notes" column because
- do not have the correct name format
- do not exist in the active directory
- did not produce an error when trying to use them for new VMs, or
- could not be validated.
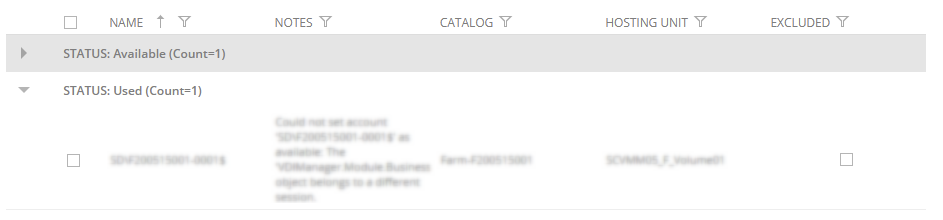
The catalog and hosting unit using an account is displayed in the list and, if the catalog or hosting unit are excluded, the "Excluded" column will be highlighted, indicating that this account might never be used while it is assigned to an excluded catalog or hosting unit.
You can mark one or more suspect or used computer accounts and set them as available again by checking their checkboxes and pressing the "Set as available" button. A new job for each user account will be enqueued.
The operation will fail if:
- the account name format is wrong.
- the account is being used by an existing VM, in this case, the VM must be specifically deleted.
You can also delete the computer accounts by checking their checkboxes and clicking the "Delete" button in the toolbar:
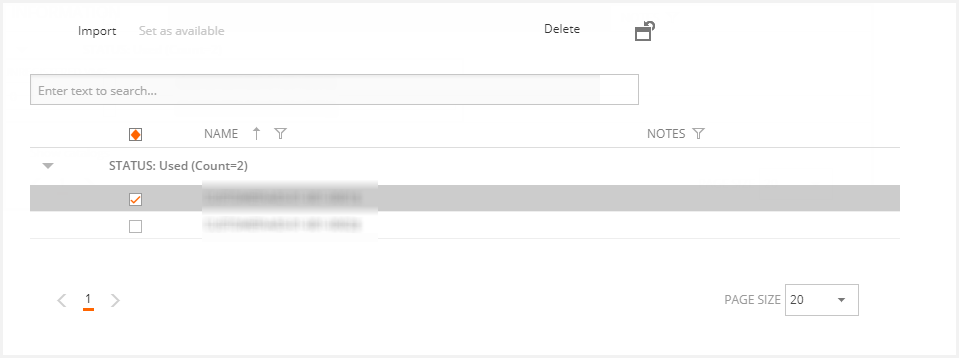
The "Import" button allows you to import new computer accounts using two methods: loading them from an Excel file, or copying/pasting them from the clipboard:
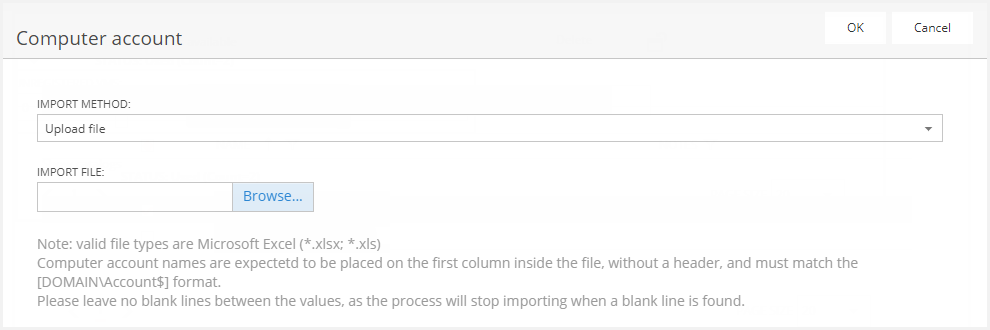
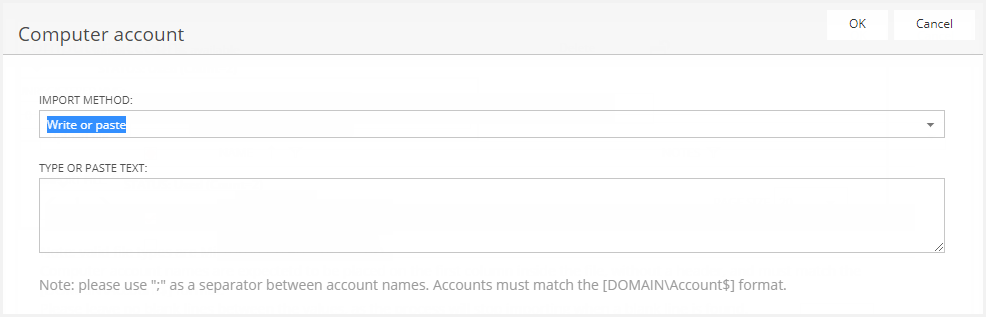
The imported accounts that do not have a correct name format, do not exist in the Active Directory, or cannot be verified, will be imported in "Suspect" status.
Remember: Before exiting the domain details, you must save the changes.
Alert “Computer accounts minimum reached for delivery group”
If a delivery group reaches the minimum available accounts configured, an alert is activated indicating the number of available accounts and the minimum for the delivery group and Application Server Farm or Virtual Desktop Template.
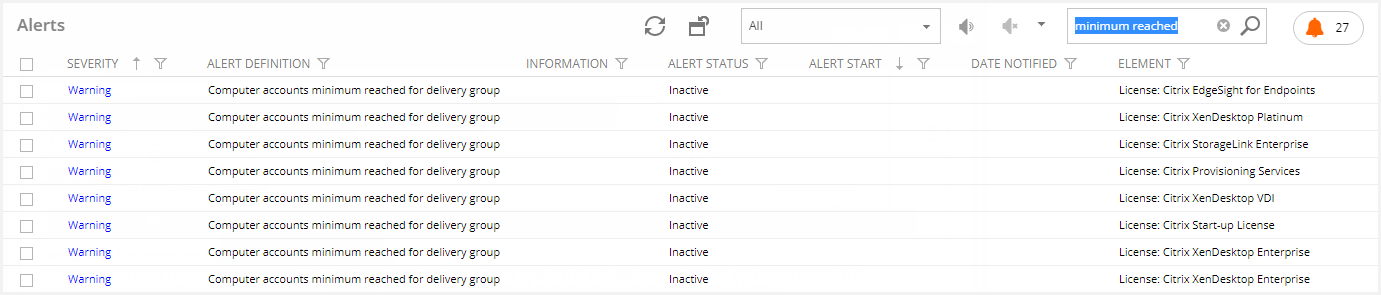
If an alert subscription has been set up, you will receive email notifications when the alert is activated.
Tenant AD configuration options
The Flexxible AD Configuration settings can be modified to enable the edition of OUs and Groups for the tenants. To do this, click on any of the Settings options in the left side menu and search for "AD Configuration" in the search box as illustrated below:
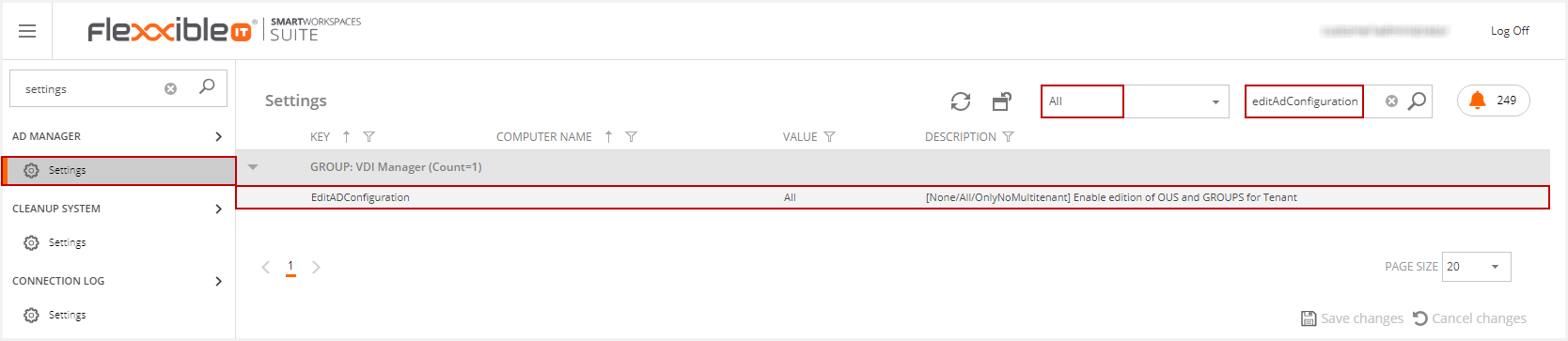
The EditADConfiguration Settings key can be set to three values:
- "None" if you don´t want the users to have permission to edit OUs and Groups in any tenant.
- "All" if you want the users to have permission to edit the OUs and Groups in all the tenants.
- "NoMultitenant" if you want the users to have permission to edit OUs and Groups on tenants that are not linked to a Multitenant domain but not on tenants that are linked to a Multitenant domain.