Introduction
A2DAgentless is a Windows service that periodically performs a reading of running applications on the computers within a specific Active Directory group in the domain where the service is running.
The A2DAgentless service performs a reading of the computers of the specified Active Directory group, and once the results are obtained, it performs an individual reading of the applications open at that particular moment. After reading the data, it carries out a persistent storage in the application’s API, which will allow it to process and display this information in the Apps2Digital application.
System requirements
- Microsoft .Net Framework 4.5.2 or above
- PowerShell 5 or above
- The service account who runs the Flexxible|Apps2Digital Agentless service must be an administrator of the machines belonging to the Active Directory group, and must have their Active Directory read permissions on.
- The service account who runs the Flexxible|Apps2Digital Agentless service must be local administrator of the machine/s where it is installed.
- The server must have WMI infrastructure installed and running
Nano Server and Serve Core editions are not supported. Some of components require graphical user interface (GUI).
Endpoint requierements
Enable firewall rule
A default firewall rule exists for WS-Management connections and it must be enabled. The name of the firewall rule is Windows Remote Management (HTTP-In) and it should be enabled on the Domain and Private profiles.
Automatically start the WinRM service
The Windows Remote Management (WS-Management) service must be started and set to Automatic (Delayed Start).
Enable WinRM remote connections
Remote connections using WS-Management must be enabled. A local policy or group policy parameter must be set to enable these connections.
The policy can be found in this path: Computer | Policies | Administrative Templates | Windows Components | Windows Remote Management (WinRM) | WinRM Service | Allow remote server management through WinRM. On some versions of Windows, the policy may be named Allow automatic configuration of listeners, but the configuration is the same.
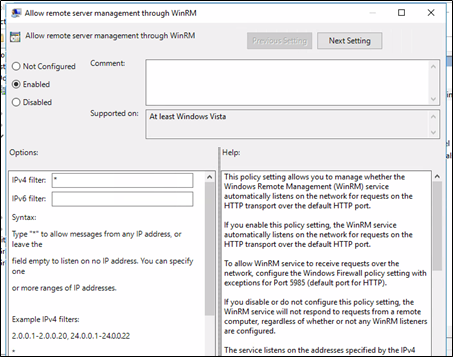
To enable WS-Management connections from remote sources you must specify a range of subnets to permit. If you want to enable connections from everywhere, you can input * in the IPv4 text field as seen in the image.
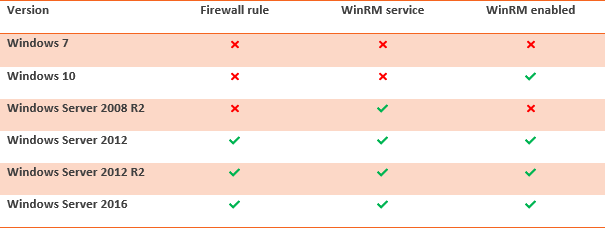
Required settings per version
The following configuration is applied to a default installation of Windows. All settings must be enabled for remote connections to work.
Active Directory
Flexxible|A2DAgentless needs to read information about groups in your Active Directory. This process will obtain all computers that exist in specific group to get applications and users information.
Keep in mind that this discovery process only inspect computers in current Active Directory. In Multi Active Directory domain scenarios, install at least one A2DAgentless on each Active Directory domain.
Install and configure
The A2DAgentless installation will be done by executing a PowerShell script that can be downloaded from the following URL:
https://apps2digitalagents.blob.core.windows.net/agentless/release/nuAppAgentlessInstaller.exe
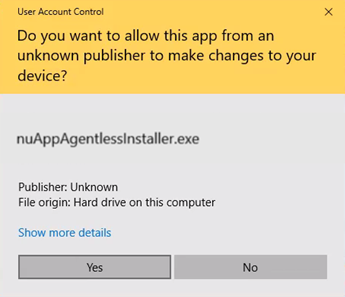
It is important to note that the application execution must be executed with elevated privileges (Administrator) when the installation program is running. Therefore, when running the installer, the following screen will be displayed:
The execution of the script with elevated privileges will request a series of parameters that will complete the service configuration:
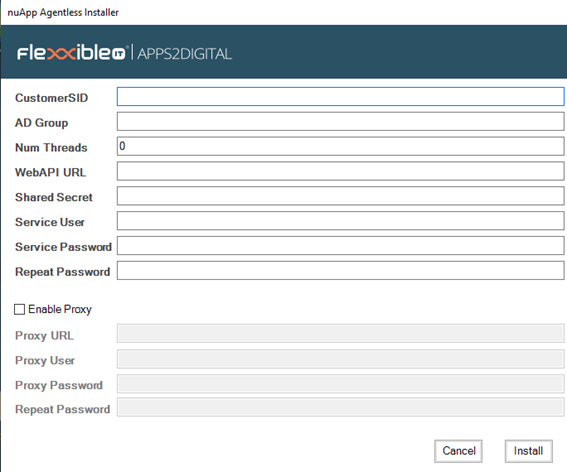
CustomerSID: Unique customer identifier provided by Flexxible IT.
AD Group: Name of the existing group in Active Directory of the company whose computers will be monitored.
Num Threads: Maximum number of threads that will be executed when executing the “Discover” of the computers that belong to the Active Directory group.
WebAPI URL: Address of the API
Shared Secret: Password that will be provided by Flexxible IT that will aim to make the communications between A2DAgentless and the API secure.
Service User: User belonging to the Active Directory of the company that will run the service. This user must be an administrator of the machines that belong to the Active Directory group, and must have Active Directory read permissions on.
Service Password: Password of the user who will run the A2DAgentless service.
Once the parameters are introduced, the A2DAgentless service will be configured and in execution mode.
The installation can be checked by verifying whether there is a service called Flexxible|Apps2Digital Agentless in the list of machine services.

The files necessary for the execution of the service will be located in %PROGRAMFILES%\A2DAgentLess
You can specify logs path in file %PROGRAMFILES%\A2DAgentLess\log4net.configure.config:
<param name="File" value="c:\logs\nuApp\A2DAgentLess.WS.Log" />
The configuration data entered in the A2DAgentless installation will be stored in the file:
%PROGRAMFILES%\A2DAgentLess\A2DAgentLess.WindowsService.exe.config
If you have entered any wrong value in the installation, just change the correct values and restart the service.
Install and upgrade
You can update your A2DAgentless launching installation method. Please, follow steps in Install and configure section of this document.
Manual installation
You can update your A2DAgentless launching installation method. Please, follow steps in Install and configure section of this document.
Auto-update
A2DAgentLess is provided with an automatic service update system. Each time Flexxible IT launches a new service update, it will be A2DAgentless itself who will download the binaries and install them, returning the service to run mode. This process is launched every 12h.
It should be noted that said update will not stop any monitoring or sending information processes.
List of technologies
This section details the proposed technologies to be used to perform the operations listed in the previous section.
Windows Management Instrumentation and Common Information Model
Common Information Model (or CIM) is a DMTF standard that provides tools to manage all kinds of different systems using a common set of commands and parameters. CIM provides a schema that you can query in all systems implementing it to obtain or set information and resources on them. At the time of this writing, the most recent version of the CIM Schema is 2.51.0. You can view all the classes contained in the schema in the following URL: http://schemas.dmtf.org/wbem/cim-html/2.50.0/
Windows Management Instrumentation (or WMI) is currently just a vendor extension of the standard CIM that provides additional information specific to Windows systems on specific CIM classes.
PowerShell remoting (tech-preview)
To run PowerShell commands on remote computers we will use PowerShell remoting. PowerShell remoting allows us to use WS-Management (WinRM) to open persistent PowerShell connections to a remote computer or execute a remote one-off command.
PowerShell remoting is available on Windows 7, Windows Server 2012 and newer versions of Windows without any additional software installation, but it may require network or service configuration, detailed in a section below.