Integrating with an Existing Active Directory Domain
Flexxible|Suite only supports Active Directories within Organizational Units built-in English. If English is not the AD language, the group "Authenticated users" won´t exist. This can lead to very poor performance.
Integrate with Active Directory Forest
In this case, during the domain integration process, a trust relationship is not needed between the resources and the customer domains. Also, all the objects or items involved such as Groups, GPOs, OUs, etc are included in the client domain. Therefore, the client is able to customize the Groups and the OUs. Apart from that, we should follow the same process we did for the integration with an Active Directory, which has already been illustrated in this article.
Remark
When you choose to integrate your Windows domain into the deployment, a series of changes are made to your domain controller to integrate it into the automatic orchestration process.
During the domain integration process for full and mixed deployments, a trust relationship will be created between the resource domain, so you'll have an environment that works in two domains:
- Desktops, application servers, and templates will be in the customer domain.
- Citrix servers, hypervisors, and the rest of the infrastructure will be in the resource domain.
Note: in full integration deployments all users, machines, GPOs, and even the infrastructure servers will be in the customer domain.
In addition, a number of requirements must be met, such as:
- Conditional forwarders are created in both domains so that they can be resolved between them (only for full and mixed deployment).
- FlexxibleIT Organizational Unit (OU) is created with full account control permissions for the FlexxibleVDIServices account. This group contains the MSA accounts used by the orchestration layer.
- The structure of OUs, groups, and users created from this OU (Desktops, AppServers, etc.) is the following:
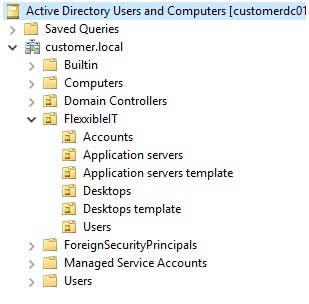
- Security groups: to manage the activation of functionalities on users and resources, new groups will be created within the base organizational unit. The list of groups to be created is as follows:
- Template Designers: users with permission to edit templates
- Users: all users in the virtualization environment
- Managers: administrators of the environment
- Remote support team: users who can provide remote assistance to other users
- Users with USB redirection: enable USB redirection
- Users with COM redirection: activation of COM redirection
- Users with LPT1 redirection: activation of LPT1 redirection
- Users with Local Units redirection: enable redirection of local units
- Users with Audio redirection: enable audio redirection
- Users with Printer redirection: enable printer redirection
- Users with TWAIN redirection: enable TWAIN redirection
- Users with Network drive redirection: enable network drive redirection
AD Integration for Flexxible|Appliances
There are two types of integration with client domains for deployments performed on Flexxible|SUITE:
- Mixed deployment: The Resource domain, which is integrated with an existing client domain gets auto-generated. A two-way Trust relationship between both domains is created.
- Full integration: No Resource domain generated, as the entire solution is installed under an existing domain. There is no trust relationship created for this deployment.
The possibility to integrate multiple domains will be enabled depending on the type of deployment:
- Enterprise Deployment, it allows integration with only ONE client domain.
-
MT Deployment(multitenant), it allows integration with multiple domains in two formats:
- Dedicated Domain, a domain will be imported from Active Directory to be totally dedicated to a single tenant. It can be a client in the DaaS environments, a site in a multisite client, a department in a large company, etc.
- Multitenant Domain, a domain will be imported enabling the multitenant functionality, which allows the orchestration of different clients (or sites, departments, etc) in the same domain isolating each tenant into a unique 'domain OU' and orchestrating all the processes related to the mentioned tenant under this specific "Base OU".
In Multitenant environments, each tenant has a tenant code which is made of three characters. Such code, which is the tenant code in a multitenant domain, also represents the name of the tenant's Base OU.
In both cases, the requirements are shown below:
Users and Groups
The following users and groups should be created for the specified domains:
The Users and Groups specific for Flexxible|SUITE can be created in any OU, although for the sake of the infrastructure management, the prefered OU would be *\VDI OS\Users.
| Account | Proposed name | Observations |
|---|---|---|
| VDI OS Administrators Group | VDI OS Administrators | Optional if there is more than one administrator. |
| VDI OS Administrator | VDIOSAdmin | Account to manage VDI OS |
| Organization | Name | Remark | Domain | Scope |
|---|---|---|---|---|
| VDI OS Services Group | VDI OS Services | Includes the MSA accounts of the VDI OS Services. | Infrastructure | Global |
| Controllers Group | DDControllers | Includes the AD accounts of the XenDesktop's Desktop Delivery Controllers which are part of the Domain infrastructure | Infrastructure | Local Domain |
| Double factor authentication Group (Deprecated 4.4) |
VDI OS Double factor Authentication | Includes the users who can start a session in their desktop via Token-Based Authentication | All the client domains | Local Domain |
| USB redirection Group | VDI OS USB redirection | Includes the users who can use USB devices in their Virtual Desktops. | All the client domains | Local Domain |
| COM redirection Group | VDI OS COM redirection | Includes the users who can use their local machine COM port in their Virtual Desktops | All the client domains | Local Domain |
| LPT1 redirection Group | VDI OS LPT1 redirection | Includes the users who can use their local machine LPT1 port in their Virtual Desktops | All the client domains | Local Domain |
| Local units redirection Group | VDI OS Local units redirection | Includes the users who can use their local machine physical disks in their Virtual Desktops | All the client domains | Local Domain |
| Audio redirection Group | VDI OS Audio redirection | Includes the users who can redirect sound audio from their Virtual Desktop to their local machine | All the client domains | Local Domain |
| Printer redirection Group | VDI OS Printer redirection | Includes the users who can use the printers connected to their local machine, in their virtual desktop | All the client domains | Local Domain |
| TWAIN redirection Group | VDI OS TWAIN redirection | Includes the users who can use the TWAIN scanners connected to their local machine, in their virtual desktop | All the client domains | Local Domain |
| Network drives redirection Group | VDI OS Network drives redirection | Includes the users who can use their local machine network units, in their virtual desktop | All the client domains | Local Domain |
| User | Name | Remark | Domain |
|---|---|---|---|
| VDI OS Administrator | VDI OSAdmin | This user is the administrator of the Flexxible|SUITE infrastructure | Infrastructure |
| Multitenant Domain AD Read Only User | VDIHandlerDaaS | Multi-client Active Directory Read-Only User | MT Domain |
| Client Domain AD Read Only User | VDIHandler | AD Read-Only User for each client | All the client domains |
| Multitenant Domain AD Write Access User | VDIHandlerDaaS | This user has permissions to edit the Multi-client Active Directory | MT Domain |
| Client Domain AD write Access User | VDIManager | AD Write Access User for each client | All the client domains |
| Managed Service Account Web1 | MSAWeb01$ | VDI OS Services Group Member. For the Flexxible|SUITE Services that are executed in their infrastructure web servers. VDI OS console application pool identity. | Infrastructure |
| Managed Service Account Web1 | MSAWeb02$ | VDI OS Services Group Member. For the Flexxible|SUITE Services that are executed in their infrastructure web servers. VDI OS console application pool identity. | Infrastructure |
| Managed Service Account Worker1 | MSAWorker01$ | VDI OS Services Group Member. For the Flexxible|SUITE Services that are executed in their infrastructure worker servers. | Infrastructure |
| Managed Service Account Worker2 | MSAWorker02$ | VDI OS Services Group Member. For the Flexxible|SUITE Services that are executed in their infrastructure worker servers. | Infrastructure |
| Managed Service Account XD1 | MSAXD01$ | VDI OS Services Group Member. For the Flexxible|SUITE Services that are executed in their infrastructure XenDesktop servers. |
Infrastructure |
| Managed Service Account XD2 | MSAXD02$ | VDI OS Services Group Member. For the Flexxible|SUITE Services that are executed in their infrastructure XenDesktop servers. |
Infrastructure |
OUs
A series of OUs are required in the client/MT domain and in the infrastructure domain as well. In the client domain, only one OU is required. In a Multitenant environment, a Base OU should be created for each tenant. For both cases, the results will be the following (See below):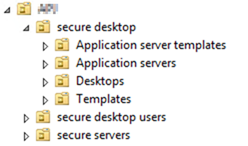
Regarding the OUs created in the infrastructure domain: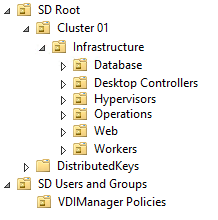
| OU | Name and Proposed Route | Comment |
|---|---|---|
| VDI OS Base OU | VDI OS | Includes the OUs that are used by VDI OS Manager |
| Infrastructure OU | VDI OS - Infrastructure | Includes the Flexxible|SUITE Infrastructure machines |
| Users OU | VDI OS - User and groups | Includes the Flexxible|SUITE Users and Groups |
Permissions
The below table includes a brief description of the privileges to be granted:
| OU Object | Group | Permissions | Remark |
|---|---|---|---|
| Infrastructure OU | VDI OS Services OU | Read Create computer objects Delete computer objects |
In the infrastructure domain with delegated privileges |
| VDI OS Base OU | VDI OS Services Group | Read Create computer/user objects Delete computer/user objects |
In MT and Client domain |
Group Directives
Several group directives should be imported to assure the right performance of Flexxible|SUITE and its relationship to some OUs (Once they have been created inside the VDI OS OU).
VDI OS OU
An OU is needed to host all the domain objects used by Flexxible|SUITE:
- OUs (children)
- Users (optional, as they would already exist in the client OUs)
- Groups used by Flexxible|SUITE
- Equipment Account
- Service Account
The OU may not be a child of the Root Domain. However, it is recommended to enable the "Block inheritance" option so that the defined GPOs are not applied accidentally at any level above the OU, except in cases, the "enforce" option has been checked intentionally.
Service Accounts
It is required to create the Managed Service Accounts needed to identify the VDI OS services.
| Account | Server | Role |
|---|---|---|
| MSADB01$ | DB01 | SQL Server |
| MSADB02$ | DB02 | SQL Server |
| MSAVSP01$ | Hypervisor01 | Hypervisor cluster or management machine |
| MSAVSP02$ | Hypervisor02 | Hypervisor cluster or management machine |
| MSAWeb01$ | Web01 | Web Server |
| MSAWeb02$ | Web02 | Web Server |
| MSAWorker01$ | Worker01 | VDI OS Orchestrator |
| MSAWorker02$ | Worker02 | VDI OS Orchestrator |
| MSAWorker03$ | Worker03 | VDI OS Orchestrator |
| MSAWorker04$ | Worker04 | VDI OS Orchestrator |
| MSAXD01$ | XD01 | XenDesktop Controller |
| MSAXD02$ | XD02 | XenDesktop Controller |
It is recommended that the “MSA” prefix is included in the accounts names, and also the name of their corresponding infrastructure server. For example, for the server DB01, the name of the MSA account should be MSADB01$.
“VDI OS Services” Group
In the OU created for Flexxible|SUITE, the group is formed by the Managed Service Account of the Flexxible|SUITE services. This group should:
- Have the MSA accounts created for our infrastructure machine included as members of the group
- Have Local Administrator privilege on the six Flexxible IT machines as the mentioned services send commands over the machines, which require privileges (to get the system uptime, analyze and start services, restart or shut down the machine, etc).
- Have Local Administrator access to the templates which use Personal vDisk. If this is not the case, Flexxible|SUITE won´t be able to process the template inventory during the Ready for Deploy process.
The “AD Accounts / VDIOSServicesGroup” parameter should be notified within the Domain\Name\Group associated with this group.
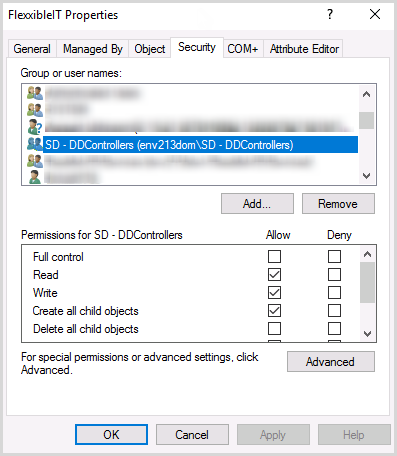
DDControllers Group
This group should be formed by the AD accounts of the Desktop Delivery Controllers for all the XenDesktop sites, as it is used to grant access to XenDesktop to create objects in the "Desktops" OU.
Once the group is created, its name will be included in the “AD Accounts / DDControllersGroup” application parameter
This group must have the following permissions on the OUs where the machines are created:
Redirection Groups
The Groups of Users to be created are:
- Double factor authentication (Deprecated 4.4)
- USB redirection
- COM redirection
- LPT1 redirection
- Local Units redirection
- Audio redirection
- Printer redirection
- TWAIN redirection
- Network drives redirection
These groups should be included in the VDI OS parameters, in the “Users policies” Group and in the VDI OS Domain properties.
Please, refer to the Active Directory Integration for FLEXXIBLE|Appliances for more information.